A complete developer guide for implementing Keccak Message Authentication Code (KMAC) in .NET applications. This guide covers everything from basic concepts to advanced implementation patterns, security considerations, and performance optimization techniques. Ideal for developers working with cryptographic authentication in .NET 9 and later versions.
Quick Summary (TL;DR ): KMAC (Keccak Message Authentication Code) is a NIST-standardized message authentication code offering quantum resistance, variable-length output, and high performance in .NET 9. This guide covers implementation, security best practices, and performance optimization techniques.
Table of Contents
- Introduction
- What is KMAC?
- Understanding KMAC Components
- KMAC Variants
- Implementation in .NET 9
- Use Cases and Applications
- Security Considerations
- Performance Characteristics
- Best Practices
- Comparison with Other MACs
- Comprehensive Error Handling and Testing
- Frequently Asked Questions
- Further Reading and Resources
- Summary
Introduction
KMAC (Keccak Message Authentication Code) is a powerful cryptographic function standardized by NIST in SP 800-185. With the introduction of KMAC support in .NET 9, developers now have access to this robust cryptographic primitive directly within the framework.
What is KMAC?
KMAC (Keccak Message Authentication Code) is a NIST-standardized cryptographic function that offers:
- Message authentication capabilities
- Variable-length output
- Support for customization strings
- Strong security guarantees
Key Terminology
| Term | Definition |
|---|---|
| KMAC | Keccak Message Authentication Code – A cryptographic function family standardized by NIST that provides message authentication capabilities. |
| KECCAK | The underlying permutation function used in SHA-3 and KMAC, providing cryptographic security through its sponge construction. |
| Customization String | An optional input that enables domain separation, allowing multiple independent KMAC instances from the same key. |
| Sponge Construction | The cryptographic primitive underlying KMAC, which alternates between absorbing input and squeezing output. |
| Domain Separation | A technique to ensure that different uses of the same cryptographic primitive remain independent. |
| Rate | The portion of the KECCAK state used for input/output operations (r). |
| Capacity | The portion of the KECCAK state reserved for security (c). |
Quick Start Guide
Basic Usage
public static class KmacQuickStart
{
// Simple authentication
public static byte[] SimpleAuthentication(string message)
{
// Generate a secure random key
byte[] key = new byte[32];
RandomNumberGenerator.Fill(key);
// Create KMAC instance and compute hash
using var kmac = new Kmac256(key);
return kmac.ComputeHash(Encoding.UTF8.GetBytes(message));
}
// Verify authentication
public static bool VerifyAuthentication(string message, byte[] key, byte[] tag)
{
using var kmac = new Kmac256(key);
var computedTag = kmac.ComputeHash(Encoding.UTF8.GetBytes(message));
return CryptographicOperations.FixedTimeEquals(computedTag, tag);
}
}Common Patterns
- Message Authentication
public class MessageAuthenticator
{
private readonly byte[] _key;
public MessageAuthenticator(byte[] key)
{
_key = key;
}
public byte[] AuthenticateMessage(string message)
{
using var kmac = new Kmac256(_key);
return kmac.ComputeHash(Encoding.UTF8.GetBytes(message));
}
public bool VerifyMessage(string message, byte[] tag)
{
var computedTag = AuthenticateMessage(message);
return CryptographicOperations.FixedTimeEquals(computedTag, tag);
}
}- Key Derivation
public class KeyDerivation
{
private readonly byte[] _masterKey;
public KeyDerivation(byte[] masterKey)
{
_masterKey = masterKey;
}
public byte[] DeriveKey(string purpose, int keyLength)
{
using var kmac = new Kmac256(_masterKey,
Encoding.UTF8.GetBytes(purpose));
return kmac.ComputeHash(Array.Empty<byte>(), keyLength);
}
}</byte>- Stream Processing
public class StreamProcessor
{
private readonly byte[] _key;
public async Task<byte[]> ProcessStreamAsync(Stream input)
{
using var kmac = new Kmac256(_key);
byte[] buffer = new byte[4096];
int bytesRead;
while ((bytesRead = await input.ReadAsync(buffer)) > 0)
{
kmac.Update(buffer.AsSpan(0, bytesRead));
}
return kmac.Final();
}
}</byte[]>Troubleshooting Guide
Common Issues and Solutions
- Invalid Key Length
// Problem: Key length too short
byte[] shortKey = new byte[16]; // Too short for KMAC256
// Solution: Use appropriate key length
byte[] properKey = new byte[32]; // 256 bits for KMAC256
RandomNumberGenerator.Fill(properKey);- Memory Management
// Problem: Key material not cleared
byte[] key = GetKey();
using var kmac = new Kmac256(key);
// Key remains in memory
// Solution: Proper cleanup
byte[] key = GetKey();
try
{
using var kmac = new Kmac256(key);
// Use KMAC
}
finally
{
CryptographicOperations.ZeroMemory(key);
}- Performance Issues
// Problem: Creating new instance for each operation
public byte[] SlowHash(byte[] data)
{
using var kmac = new Kmac256(_key); // New instance each time
return kmac.ComputeHash(data);
}
// Solution: Reuse instance with proper synchronization
private readonly Kmac256 _kmac;
private readonly object _lock = new();
public byte[] FastHash(byte[] data)
{
lock (_lock)
{
_kmac.Initialize();
return _kmac.ComputeHash(data);
}
}Performance Troubleshooting
- Memory Allocation
public class PerformanceOptimizedKmac
{
private readonly ArrayPool<byte> _bufferPool;
public byte[] ComputeHash(byte[] data)
{
var buffer = _bufferPool.Rent(Math.Min(data.Length, 81920));
try
{
// Use pooled buffer
return ProcessWithBuffer(data, buffer);
}
finally
{
_bufferPool.Return(buffer);
}
}
}</byte>- Parallel Processing
public class ParallelKmac
{
private readonly int _parallelism;
private readonly byte[] _key;
public async Task<byte[]> ProcessLargeData(byte[] data)
{
var chunks = data.Chunk(data.Length / _parallelism);
var tasks = chunks.Select(chunk => Task.Run(() =>
{
using var kmac = new Kmac256(_key);
return kmac.ComputeHash(chunk);
}));
var results = await Task.WhenAll(tasks);
using var finalKmac = new Kmac256(_key);
return finalKmac.ComputeHash(CombineResults(results));
}
}</byte[]>Security Audit Checklist
public class KmacSecurityAudit
{
public SecurityAuditResult PerformAudit()
{
return new SecurityAuditResult
{
KeyManagement = CheckKeyManagement(),
MemoryHandling = CheckMemoryHandling(),
ThreadSafety = CheckThreadSafety(),
ErrorHandling = CheckErrorHandling(),
ConfigurationSecurity = CheckConfiguration()
};
}
private bool CheckKeyManagement()
{
// Verify:
// 1. Key length >= 256 bits for KMAC256
// 2. Secure key generation
// 3. Key rotation policy
// 4. Secure key storage
// 5. Key cleanup procedures
}
private bool CheckMemoryHandling()
{
// Verify:
// 1. Sensitive data cleanup
// 2. Buffer pooling
// 3. Stack vs heap usage
// 4. Memory pressure handling
}
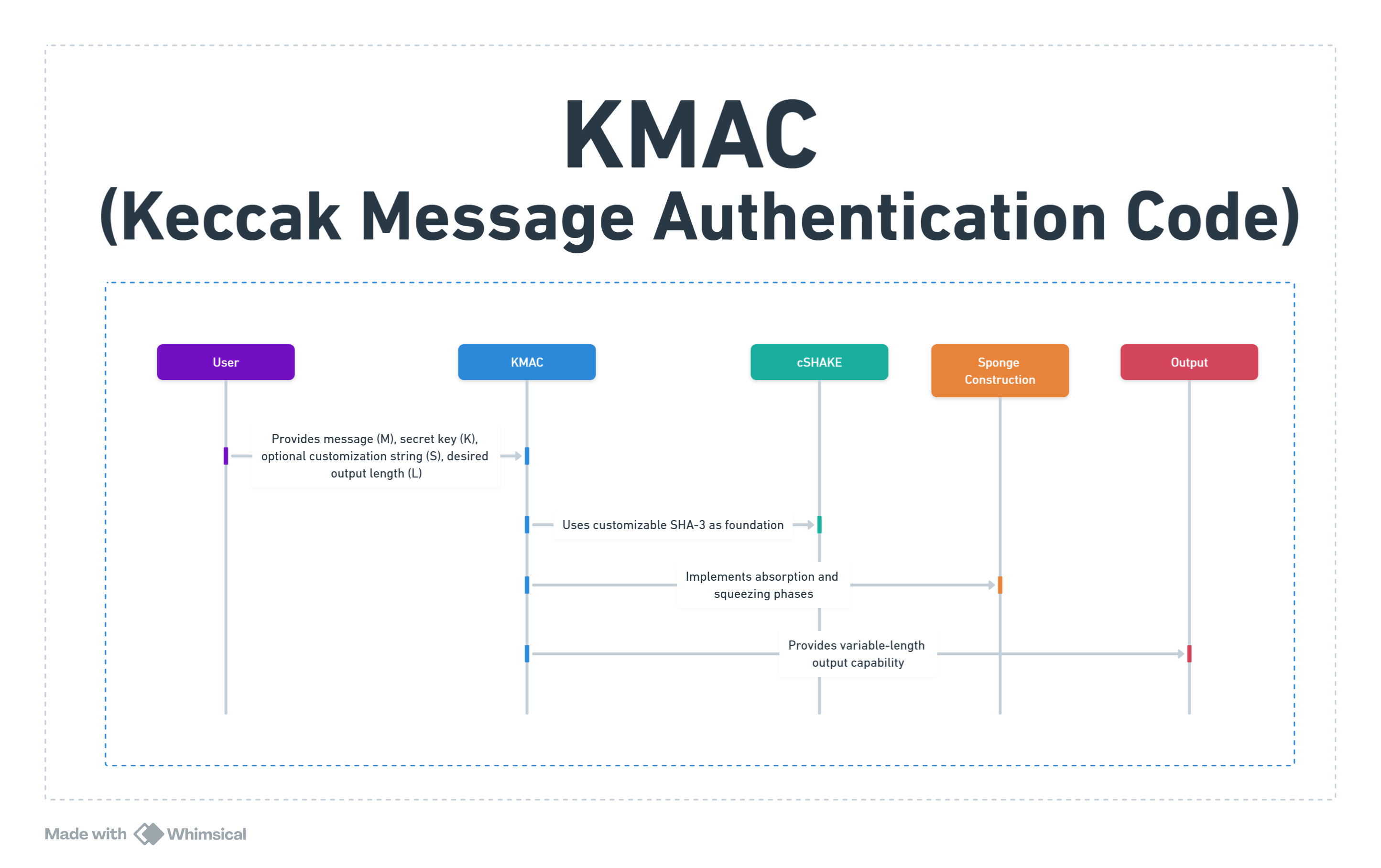
}Understanding KMAC Components
Core Components
- KECCAK Permutation
- The underlying cryptographic sponge function
- 1600-bit state organized as 5×5×64 bits
- Key Input
- Secret key material
- Recommended lengths: 128, 256, or 512 bits
- Customization String
- Optional parameter for domain separation
- Allows multiple KMAC instances from the same key
Internal Structure
KMAC uses a structured internal design that processes inputs in the following sequence:
- Initialization Phase
- Initialize the KECCAK state to all zeros
- Absorb the encoded rate and capacity parameters
- Process function name (“KMAC”)
- Key Processing
- Encode and absorb the key length
- Absorb the encoded key material
- Pad to block boundary
- Customization String Processing
- Encode and absorb customization string length
- Absorb the encoded customization string
- Apply padding
- Message Processing
- Encode and absorb message length
- Process message blocks sequentially
- Apply padding function
- Output Generation
- Encode desired output length
- Generate output bits through squeezing
- Truncate to requested length
The internal state transitions follow the sponge construction paradigm:
- Absorption phase: XOR input blocks into state
- Permutation phase: Apply KECCAK-p[1600]
- Squeezing phase: Extract output bits
KMAC Variants
KMAC comes in two standardized variants:
KMAC128
- Based on KECCAK-128
- Security strength up to 128 bits
- Recommended for most general-purpose applications
- Default output length of 256 bits
- Suitable for generating keys up to 128 bits
KMAC256
- Based on KECCAK-256
- Security strength up to 256 bits
- Recommended for applications requiring higher security
- Default output length of 512 bits
- Suitable for generating keys up to 256 bits
Both variants support:
- Variable-length outputs
- The same customization string functionality
- Identical internal structure and processing steps
The main differences lie in:
- Internal capacity (c) and rate (r) parameters
- Security strength guarantees
- Default output lengths
- Recommended key sizes
Implementation in .NET 9
.NET 9 introduces native KMAC support through the following classes:
Core Classes
- Kmac128
- Primary implementation for KMAC-128
- Provides 128-bit security strength
- Located in System.Security.Cryptography namespace
using var kmac = new Kmac128(key); byte[] tag = kmac.ComputeHash(data); - Kmac256
- Primary implementation for KMAC-256
- Provides 256-bit security strength
- Located in System.Security.Cryptography namespace
using var kmac = new Kmac256(key); byte[] tag = kmac.ComputeHash(data);
Key APIs and Methods
- Constructor Options
// Basic constructor with key public Kmac128(byte[] key) // Constructor with key and custom string public Kmac128(byte[] key, byte[] customization) // Constructor with key, custom string, and output length public Kmac128(byte[] key, byte[] customization, int outputLength) - Core Methods
// Single-shot computation byte[] ComputeHash(byte[] data) // Streaming computation void Initialize() void Update(byte[] data) byte[] Final() - Helper Properties
int HashSize { get; } // Output size in bits int BlockSize { get; } // Internal block size bool IsDisposed { get; } // Disposal status
Usage Examples
- Basic Authentication
byte[] key = new byte[32]; // Generate appropriate key byte[] message = GetMessage(); using var kmac = new Kmac128(key); byte[] tag = kmac.ComputeHash(message); - Custom Output Length
byte[] key = new byte[32]; byte[] customization = "MyApp:Context1"u8.ToArray(); using var kmac = new Kmac256(key, customization, outputLength: 64); byte[] tag = kmac.ComputeHash(message); - Streaming API
using var kmac = new Kmac256(key); kmac.Initialize(); foreach (var chunk in messageChunks) { kmac.Update(chunk); } byte[] tag = kmac.Final();
Important Considerations
- Key Management
- Use cryptographically secure random keys
- Protect keys in secure storage
- Rotate keys according to security policy
- Never reuse keys across different contexts
- Performance Optimization
- Use streaming API for large messages
- Reuse KMAC instances when possible
- Consider buffer pooling for large-scale operations
- Security Best Practices
- Use customization strings for domain separation
- Validate output lengths match security requirements
- Implement constant-time comparison for tags
- Always dispose of KMAC instances properly
- Error Handling
try { using var kmac = new Kmac256(key); byte[] tag = kmac.ComputeHash(message); } catch (ArgumentNullException) { // Handle null key or message } catch (ArgumentException) { // Handle invalid parameters } catch (CryptographicException) { // Handle cryptographic operation failures } finally { // Ensure proper cleanup } - Thread Safety
- Do not share KMAC instances across threads
- Use separate instances for parallel operations
- Consider thread-local storage when needed
// Thread-safe usage example private static ThreadLocal<kmac128> threadLocalKmac = new(() => new Kmac128(masterKey)); public byte[] ComputeThreadSafeTag(byte[] data) { using var kmac = threadLocalKmac.Value; return kmac.ComputeHash(data); }</kmac128> - Memory Management
byte[] sensitiveKey = GetKey(); try { using var kmac = new Kmac256(sensitiveKey); byte[] tag = kmac.ComputeHash(message); return tag; } finally { CryptographicOperations.ZeroMemory(sensitiveKey); } - Interoperability
- Use standard output lengths when sharing tags across systems
- Document customization strings in API contracts
- Consider encoding requirements for cross-platform scenarios
// Interoperable usage with fixed output length byte[] key = new byte[32]; byte[] customization = "org.example.protocol.v1"u8.ToArray(); using var kmac = new Kmac256(key, customization, outputLength: 32); byte[] standardTag = kmac.ComputeHash(message); - Versioning and Compatibility
- Maintain version compatibility in customization strings
- Consider fallback mechanisms for older systems
- Document version dependencies clearly
// Version-aware KMAC usage private const string CurrentVersion = "v2"; private static readonly byte[] LegacyCustomization = "org.example.v1"u8.ToArray(); private static readonly byte[] CurrentCustomization = $"org.example.{CurrentVersion}"u8.ToArray(); public byte[] ComputeVersionedTag(byte[] data, string targetVersion) { byte[] customization = targetVersion == "v1" ? LegacyCustomization : CurrentCustomization; using var kmac = new Kmac256(key, customization); return kmac.ComputeHash(data); }
- Testing and Validation
// Test vector validation public void ValidateKmacImplementation() { byte[] key = new byte[32]; byte[] message = "test message"u8.ToArray(); byte[] expectedTag = GetKnownGoodTag(); // From test vectors using var kmac = new Kmac256(key); byte[] actualTag = kmac.ComputeHash(message); if (!CryptographicOperations.FixedTimeEquals(expectedTag, actualTag)) throw new CryptographicException("KMAC implementation validation failed"); } - Documentation and Maintenance
- Document key derivation procedures
- Maintain clear API documentation
- Include security considerations in comments
- Keep implementation details up to date
/// <summary> /// Derives a cryptographic key using KMAC256 as a key derivation function. /// </summary> /// <param name="masterKey"/>The master key used for derivation /// <param name="context"/>Application-specific context string /// <param name="derivedKeyLength"/>Length of the derived key in bytes /// <returns>The derived cryptographic key</returns> /// <remarks> /// Security Considerations: /// - Master key should be randomly generated and securely stored /// - Context should be unique per key derivation purpose /// - Derived key length should match security requirements /// </remarks> public byte[] DeriveKey(byte[] masterKey, string context, int derivedKeyLength) { byte[] contextBytes = Encoding.UTF8.GetBytes(context); using var kmac = new Kmac256(masterKey, contextBytes, derivedKeyLength); // Use a counter as input to ensure uniqueness byte[] counter = BitConverter.GetBytes(1); return kmac.ComputeHash(counter); }
Use Cases and Applications
KMAC finds application in various cryptographic scenarios:
- Message Authentication
- Ensuring message integrity
- Verifying data authenticity
- Protecting against tampering
- Key Derivation
- Generating cryptographic keys
- Creating session keys
- Deriving multiple keys from a master key
- Pseudorandom Generation
- Creating deterministic random values
- Generating unique identifiers
- Seeding random number generators
- Digital Signatures
- Auxiliary function in signature schemes
- Creating commitment schemes
- Binding commitments
- Password Hashing
- Secure password storage
- Key stretching
- Salt handling
- Protocol Integration
- TLS protocol extensions
- Secure communication channels
- Authentication protocols
- Blockchain Applications
- Transaction signing
- Block validation
- State verification
- IoT Security
- Resource-constrained authentication
- Secure firmware updates
- Device attestation
Implementation Examples
Here are concrete examples demonstrating KMAC usage in different scenarios:
- Message Authentication Example
// Authenticate a message byte[] key = new byte[32]; byte[] message = GetMessage(); using var kmac = new Kmac256(key); byte[] authTag = kmac.ComputeHash(message); - Key Derivation Example
// Derive multiple keys from master key byte[] masterKey = new byte[32]; byte[] context1 = "encryption_key"u8.ToArray(); byte[] context2 = "signing_key"u8.ToArray(); using var kdf1 = new Kmac256(masterKey, context1, outputLength: 32); byte[] encryptionKey = kdf1.ComputeHash(Array.Empty<byte>()); using var kdf2 = new Kmac256(masterKey, context2, outputLength: 32); byte[] signingKey = kdf2.ComputeHash(Array.Empty<byte>());</byte></byte> - Password Hashing Example
// Hash password with salt byte[] password = GetPasswordBytes(); byte[] salt = GetRandomSalt(); byte[] context = "pwd_hash"u8.ToArray(); using var kmac = new Kmac256(salt, context, outputLength: 32); byte[] passwordHash = kmac.ComputeHash(password); - Blockchain Transaction Signing
// Sign transaction data byte[] privateKey = GetPrivateKey(); byte[] transactionData = GetTransactionData(); byte[] context = "tx_sign"u8.ToArray(); using var kmac = new Kmac256(privateKey, context); byte[] signature = kmac.ComputeHash(transactionData); - File Integrity Verification
// Compute and verify file hash byte[] key = new byte[32]; byte[] context = "file_hash"u8.ToArray(); using var kmac = new Kmac256(key, context); using var fileStream = File.OpenRead("data.bin"); kmac.Initialize(); byte[] buffer = new byte[4096]; int bytesRead; while ((bytesRead = fileStream.Read(buffer, 0, buffer.Length)) > 0) { kmac.Update(buffer.AsSpan(0, bytesRead)); } byte[] fileHash = kmac.Final(); - Secure Random Number Generation
// Generate cryptographic random numbers byte[] seed = new byte[32]; RandomNumberGenerator.Fill(seed); byte[] context = "prng"u8.ToArray(); using var kmac = new Kmac256(seed, context); byte[] randomBytes = kmac.ComputeHash(BitConverter.GetBytes(DateTime.UtcNow.Ticks)); - Key Derivation
// Derive encryption keys from master key byte[] masterKey = new byte[32]; byte[] salt = new byte[16]; RandomNumberGenerator.Fill(salt); byte[] context = "key_derivation"u8.ToArray(); using var kmac = new Kmac256(masterKey, context); kmac.Initialize(); kmac.Update(salt); byte[] derivedKey = kmac.Final(outputLength: 32); // 256-bit derived key - Password Hashing
// Hash password with salt byte[] passwordBytes = Encoding.UTF8.GetBytes(password); byte[] salt = new byte[16]; RandomNumberGenerator.Fill(salt); byte[] context = "pwd_hash"u8.ToArray(); using var kmac = new Kmac256(salt, context); byte[] passwordHash = kmac.ComputeHash(passwordBytes);
Comparison with Other MACs
KMAC vs HMAC
- Security Properties
Property KMAC HMAC ---------------------------------------------------------- Security Basis KECCAK (SHA-3) Hash Function (typically SHA-2) Length Extension Inherently Resistant Requires Additional Protection Quantum Resistance Higher Lower Key Size Flexibility Unlimited Limited by Hash Function Output Size Variable Fixed by Hash Function
- Performance Characteristics
Metric KMAC HMAC ---------------------------------------------------------- Small Messages Faster Slightly Slower Large Messages Similar Similar Parallel Processing Better Limited Memory Usage Lower Higher
- Implementation Complexity
// KMAC Implementation using var kmac = new Kmac256(key); byte[] kmacTag = kmac.ComputeHash(data, outputLength: 32); // HMAC Implementation using var hmac = new HMACSHA256(key); byte[] hmacTag = hmac.ComputeHash(data);
KMAC vs CMAC
- Use Cases
Aspect KMAC CMAC ---------------------------------------------------------- Block Size Variable Fixed (Block Cipher) Primary Use General Purpose Block Cipher Based Key Derivation Excellent Limited Stream Processing Efficient Less Efficient
- Performance Trade-offs
// KMAC Streaming Example using var kmac = new Kmac256(key); kmac.Initialize(); foreach (var chunk in dataChunks) { kmac.Update(chunk); } byte[] kmacTag = kmac.Final(); // CMAC Requires Full Data using var cmac = new AesCmac(); byte[] cmacTag = cmac.ComputeMac(key, allData);
KMAC vs Poly1305
- Characteristics Comparison
Feature KMAC Poly1305 ---------------------------------------------------------- Design Purpose General Purpose AEAD Constructions Performance Good All-Around Optimized for Short Messages Implementation Software Friendly Hardware Acceleration Common Security Proof Strong Based on Different Assumptions
- Usage Patterns
// KMAC for General Authentication using var kmac = new Kmac256(key); byte[] kmacTag = kmac.ComputeHash(message); // Poly1305 Typically Used with ChaCha20 using var poly = new ChaCha20Poly1305(key); byte[] polyTag = poly.Encrypt(nonce, message, null, tag);
Migration Considerations
- From HMAC to KMAC
public class MacMigration { // Legacy HMAC implementation public byte[] ComputeLegacyHmac(byte[] key, byte[] data) { using var hmac = new HMACSHA256(key); return hmac.ComputeHash(data); } // New KMAC implementation public byte[] ComputeNewKmac(byte[] key, byte[] data) { using var kmac = new Kmac256(key); return kmac.ComputeHash(data, outputLength: 32); // Match HMAC-SHA256 length } // Gradual migration helper public byte[] ComputeMacWithVerification(byte[] key, byte[] data, bool useKmac) { if (useKmac) { var kmacResult = ComputeNewKmac(key, data); // Verify against legacy during migration var hmacResult = ComputeLegacyHmac(key, data); Debug.Assert(CryptographicOperations.FixedTimeEquals( kmacResult, hmacResult)); return kmacResult; } return ComputeLegacyHmac(key, data); } }
Frequently Asked Questions
General Usage
Q: When should I use KMAC instead of HMAC? A: Choose KMAC when you need:
- Quantum-resistant security
- Variable-length output
- Built-in domain separation through customization strings
- Protection against length extension attacks
Q: What key size should I use for KMAC256? A: For KMAC256, use a minimum key size of 32 bytes (256 bits). For additional security margin, 64 bytes (512 bits) is recommended.
Q: Is KMAC thread-safe? A: No, KMAC instances are not thread-safe. Each thread should use its own instance or implement proper synchronization.
Implementation
Q: How do I handle key rotation with KMAC? A: Implement key rotation using a pattern like:
public class KmacKeyRotation
{
private readonly TimeSpan _rotationInterval = TimeSpan.FromDays(30);
private byte[] _currentKey;
private readonly object _keyLock = new();
public void RotateKey()
{
lock (_keyLock)
{
var newKey = new byte[32];
RandomNumberGenerator.Fill(newKey);
var oldKey = _currentKey;
_currentKey = newKey;
if (oldKey != null)
CryptographicOperations.ZeroMemory(oldKey);
}
}
}Q: How do I implement streaming with KMAC? A: Use the Initialize/Update/Final pattern:
using var kmac = new Kmac256(key);
kmac.Initialize();
while (HasMoreData())
{
kmac.Update(GetNextChunk());
}
byte[] tag = kmac.Final();Security
Q: Is KMAC quantum-resistant? A: Yes, KMAC provides post-quantum security against known quantum attacks, with KMAC256 offering stronger quantum resistance than KMAC128.
Q: How do I securely store KMAC keys? A: Store keys using platform-specific secure storage:
- Windows: Data Protection API (DPAPI)
- Linux: Secret Service API
- Cross-platform: Azure Key Vault or hardware security modules (HSMs)
Related Topics
Cryptographic Primitives
- SHA-3 (Secure Hash Algorithm 3)
- The underlying hash function family for KMAC
- NIST standardized (FIPS 202)
- Quantum-resistant design
Key Management
- NIST SP 800-57: Key Management Guidelines
- Best practices for cryptographic key management
- Key lifecycle recommendations
- Security strength considerations
Message Authentication
- NIST SP 800-185: SHA-3 Derived Functions
- Official KMAC specification
- Implementation guidelines
- Security analysis
Related .NET APIs
- System.Security.Cryptography Namespace
- HashAlgorithm base class
- KeyedHashAlgorithm implementation
- Cryptographic random number generation
Further Reading and Resources
Official Documentation and Standards
- NIST SP 800-185: SHA-3 Derived Functions
- Official KMAC specification and implementation guidelines
- Security analysis and recommendations
- Test vectors and validation procedures
- .NET Cryptography Documentation
- Official .NET cryptography implementation guidelines
- Best practices for key management
- Security considerations for .NET applications
Security Standards and Best Practices
- NIST Cryptographic Standards
- Current cryptographic standards
- Implementation guidance
- Security requirements
- Common Criteria Protection Profiles
- Security certification requirements
- Evaluation criteria
- Compliance guidelines
Related Technologies
- SHA-3 Standard (FIPS 202)
- Understanding the underlying KECCAK algorithm
- Implementation details of the sponge construction
- Security proofs and analysis
- Post-Quantum Cryptography
- Future-proofing cryptographic implementations
- Quantum resistance considerations
- Emerging standards and recommendations
Summary
The KMAC (Keccak Message Authentication Code) implementation in .NET 9 represents a significant advancement in cryptographic capabilities, offering developers a NIST-standardized solution that combines security, flexibility, and performance. Built on the KECCAK (SHA-3) algorithm, KMAC provides robust security guarantees including quantum resistance and inherent protection against length extension attacks.
The native .NET implementation offers comprehensive features including variable output lengths, customization strings for domain separation, and efficient streaming capabilities for handling large datasets. Through proper implementation of the provided patterns—from basic authentication to advanced streaming operations—developers can ensure both security and performance requirements are met.
Key considerations include proper key management, memory handling, and thread safety, all of which are supported through built-in features and documented best practices. The framework’s error handling mechanisms and testing capabilities enable robust application development, while the clear migration paths from other MAC algorithms facilitate seamless integration into existing systems.
As hardware support continues to grow and adoption increases, KMAC’s role in modern cryptographic systems is expected to expand, making it a forward-looking choice for new implementations requiring strong security guarantees with flexible performance characteristics.
Happy Learning, @devsdaily